
VulnerabilitiesPrevent Remote Code Execution (RCE) Attacks in Your Node.js Project
The Remote Code Execution (RCE) attack, which allows an attacker to execute arbitrary code on a vulnerable server, is one of the most dangerous types of attacks. Unfortunately, as Node.js developers, we frequently rely on a large number of open-source libraries to develop our projects, and these libraries can introduce vulnerabilities that hackers can exploit. In this article, we'll talk about the threat of RCE attacks in Node.js projects and introduce PrivJs Safe, a new service that can help protect your projects from malicious and vulnerable npm packages.
What exactly is an RCE attack?
An RCE attack is one in which an attacker can execute arbitrary code on a remote server. This can occur when a vulnerability exists in a piece of software used by the server, in javascript projects it could be mainly due to vulnerable dependencies or unhandled `eval()` functions. This is a pretty serious vulnerability because if an attacker gains access to the server, they can do almost anything, from stealing sensitive data to taking complete control of the system.
Vulnerable Dependencies in Node.js Projects: What You Should Know
Node.js is a popular platform for developing web applications and backends that is widely used in the industry. The vast ecosystem of open-source libraries that developers can use to quickly and easily build out functionality is one of the reasons for its popularity. However, relying on so many libraries has the disadvantage of introducing severe vulnerabilities into your project.
The jsonwebtoken library, which is commonly used to handle JSON Web Tokens (JWT) in Node.js projects, is a recent example of this. This library was recently discovered to have a critical RCE vulnerability, allowing an attacker to execute arbitrary code on any server running an affected version of the library. jsonwebtoken is downloaded over 10 million times per week, making it one of the most popular packages in the nodejs ecosystem. This demonstrates how vulnerable popular libraries can be, and why it's critical to keep our dependencies up to date and secure. Jsonwebtoken is not alone, there are thousands of such vulnerable packages in the javascript ecosystem - which are risky for your projects and your organization.
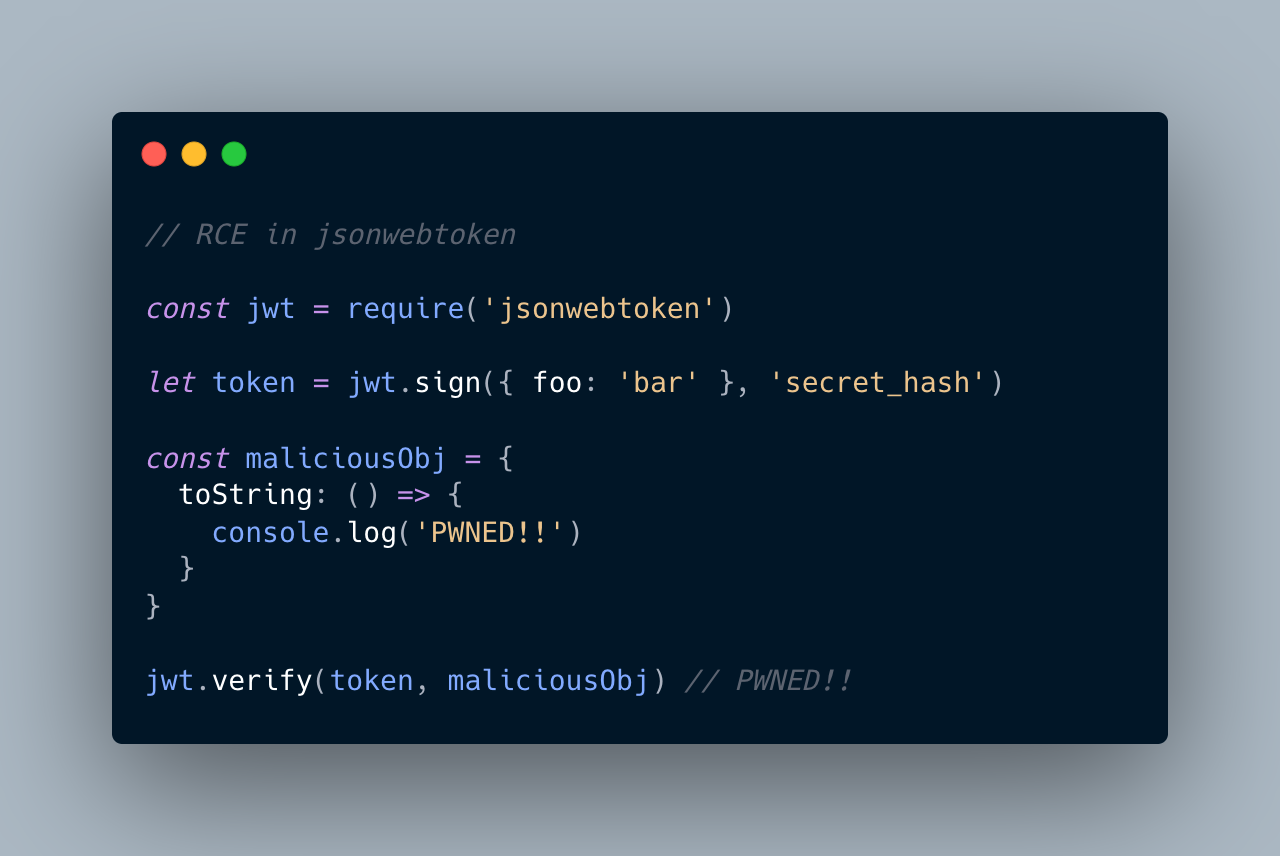
Introducing PrivJs Safe
Fortunately, there is a solution to this issue. PrivJs Safe is a new service that assists developers in avoiding vulnerable npm packages and protecting their projects from dependency-induced vulnerabilities, including XSS and RCE attacks. PrivJs Safe acts as a middleware between your computer and open-source registry, and prevents the installation of insecure packages. This eliminates the risk of missing a critical security update or inadvertently introducing a vulnerable dependency into your project.
To use PrivJs Safe, sign up at https://safe.privjs.com/signup and simply run the following two commands:
$ npm config set registry https://secure.privjs.com$ npm config set //secure.privjs.com/: _authToken <your-token-here>As simple as that, PrivJs Safe will then secure all subsequent installations on your machine. If you wish to use in a specific project, add the following to your .npmrc file:
registry=https://secure.privjs.com
//secure.privjs.com/:_authToken=xxxx-yyyy-zzzzReplace xxxx-yyyy-zzzz with your token. Easy!
Conclusion
To summarize, RCE attacks pose a significant risk to the security of our applications and systems. We rely heavily on open-source libraries to build our projects as Node.js developers, and these libraries can introduce vulnerabilities that attackers can exploit. PrivJs Safe is an effective solution to this problem that helps to ensure the security of your project. PrivJs Safe provides peace of mind by preventing the installation of vulnerable npm packages, allowing you to avoid introducing security risks into your project. Give it a try today and build code without worrying about security issues.